Spyse is a powerful cyberspace search engine which combines several data gathering tools into a full-service platform. For people tasked with data gathering, Spyse alleviates the need of having multiple tabs open on random OSINT data sources.
What makes Spyse such a useful cybersecurity tool, is that they implement a ready-database from which the user can draw data. This database contains massive amounts of internet data useful for reconnaissance, infrastructure scanning, and finding possible attack vectors.
Read on to learn about how Spyse innovates the data gathering process and offers unreal improvements in the workflows of cybersecurity specialists, pentesters and beyond.
How Mass Data Gets Gathered
Spyse use a sophisticated system of self-developed scanners, each of which are tailored towards gathering specific information from the internet. Scanners work uninterruptedly and pick up data from different sources, verifying the datasets to ensure data authenticity.
To scan the entire world unrestricted, Spyse uses a global server distribution system of fifty servers. As a result, Spyse’s scanners bypass area scanning restrictions and blocking from internet service providers. Not only does this make for more precise data, but just more data overall.

After scanning, data is interlinked to show relationships between different internet entities. Users can browse datasets freely, opening up various opportunities to finding interesting target-connected data. This also makes for a fantastic way to conduct business analysis based on mass data.
Largest Database on the Web
The database is Spyse’s greatest asset. It allows users to perform reconnaissance tasks by gathering data straight from a ready pool. This means no more manual scanning.
To provide this level of flexibility, Spyse stores hot data in a system of fifty highly functioning servers and breaks up the data into 250 shards, which makes for about 7 billion documents overall. This is one of the largest databases of its kind on the internet.
How It Works: Web Interface, API, Python
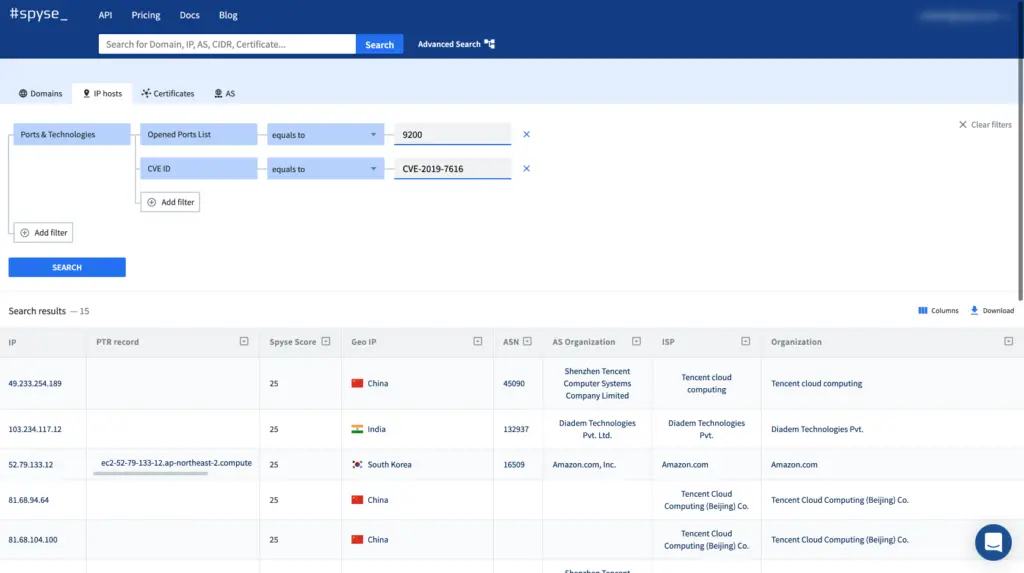
Spyse’s web interface looks like a familiar search engine tailored for cybersecurity. You perform a search, add filters if needed, and results return neatly organized into tables. This is so to help avoid scrolling through large datasets. These tables present information which can easily be filtered out to find something specific. It’s a cohesive data browsing experience, and very straightforward to use. Spyse are not greedy and have a function to let you download the data and use it offline.
They also have an API, which comes with a documentation on Swagger. It’s very flexible and easy to work with, with the many methods you can use described on the API section of Spyse’s website.
For those looking for a command line interface, Spyse doesn’t have one yet, but they do have a few Python wrappers. The wrapper was designed by outsourced developers, whose work many pentesters will be familiar with.
Productivity Enhancements
Spyse users can perform quick infrastructure scans by using the Scoring feature. It compares all found data with the most trustful CVE databases, assigning each internet entity a security rating of 0-100. Users can then explore expanded information on each vulnerability, sort targets by the level of threat, and search for vulnerable elements using the security rating or CVE id.

The advanced search tool is a live filter used for precision scanning. As you add search parameters, the program removes irrelevant results and helps direct your search towards precisely the data you need. With the use of advanced search, you don’t have to scroll through results and organize massive datasets. Using just two filters users are able to find IP’s that have specific open ports and vulnerabilities on them related to the technologies found on these ports.
*Only registered users are able to see the results.
Powerful Tool for All Cybersec Specialists
Spyse can be a very powerful asset for finding vulnerabilities, attaining data on targets, and performing business analysis. Security specialists can use Spyse to automate processes like data gathering, saving up lots of time, and potentially preventing damaging data leaks. Pentesters can also perform mock attacks at an advanced pace and remain invisible when entering a system.
In addition to walling off hackers, this service can be of great benefit to bug bounty hunters, who can use it to quickly build target lists, avoid rate limits, and use it as an alternative to methods which are prohibited by bug bounty contracts.



![Guide To Using JCP Kiosk – [ Features & Benefits ]](https://thefutureofthings.com/wp-content/uploads/2024/03/image-4-358x358.png)





