Photo by Sora Shimazaki from Pexels There are many cybercriminals out there in the world. They target individuals, small, medium, and large businesses to extort information and money. It is essential to understand how cybercriminals can hack your devices and network and prepare ...
Securing Your Business from Common Cyberattack Methods
Image by Biljana Jovanovic from Pixabay With business moving increasingly online, cybersecurity is becoming more critical than ever before. A lot of cybersecurity information is geared towards helping enterprises, and the average small business owner can feel left out. Most ...
WHOIS History Enriches Cyber Threat Intelligence
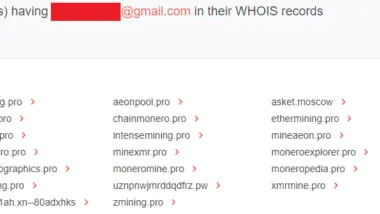
Mitigating malicious cyber events entails gathering the right information. A wide variety of cyber threat intelligence sources may not be enough, unless properly correlated, as security teams could end up with so much information. As such, it is better to ...
The Modern Guide in Safeguarding Your Business Against Cyber-Attacks
There’s no doubt that cybersecurity really has entered a league of its own over the last few years. Once upon a time companies and individuals might not have given it a second thought, but now it is at the forefront ...
Ways to Improve Your Penetration Testing Success Rates
67% of businesses that fall victim to ransomware attacks tend to lose part or all of their corporate data, according to the PC world website. One in every four companies will spend several weeks trying to regain access to their ...
Cybercriminals and Account Takeovers
One of the most important parts of managing your company’s website is keeping your users’ information safe. Part of this is making sure unauthorized people don’t have access to user accounts which can include personal information and access to their ...
Cyber Security: Password Protected
You turn on your computer and you are prompted for a username and password. The same happens when you open your email account. I know it is rather obvious to you right now, but allow me to emphasize the importance ...