Mitigating malicious cyber events entails gathering the right information. A wide variety of cyber threat intelligence sources may not be enough, unless properly correlated, as security teams could end up with so much information. As such, it is better to ensure that threat intelligence sources can provide context around cyber events. An intelligence source worth looking into is domain WHOIS history.
WHOIS history by providers like https://whois-history.whoisxmlapi.com/ enables security teams to track changes in the ownership of a suspicious domain name. By doing so, they can find associated domains and avoid related cyber events. We illustrate how domain WHOIS history can enrich threat intelligence in this post.
Unveiling More IoCs in the Monero Android Mining Malware
HiddenMalware is an Android malware that uses victims’ central processing unit (CPU) power to mine Monero (XMR). The malware hides behind seemingly legitimate application updates on Google Play and other marketplaces. With the implementation of “bring your own device (BYOD)” in several organizations, it has become essential to detect indicators of compromise (IoCs) and gather as much intelligence about HiddenMalware and others like it.
Among the IoCs for the Monero-mining malware, according to IBM X-Force Exchange, are:
- monero[.]hashvault[.]pro
- pool[.]minergate[.]com
When security teams are alerted to cyber incidents involving these domains, the best practice is to block access to and from them immediately. However, it would also be wise to gather more information to find related data that could lead to more IoCs.
WHOIS History and Domains Associated with monero[.]hashvault[.]pro
For the subdomain monero[.]hashvault[.]pro, a WHOIS lookup would only show that the registrant is a “private person” from Russia. However, domain WHOIS history reveals the last registrant’s name and the same province in Russia from October 2017 until the WHOIS record was redacted in May 2018.
A Gmail address was also indicated in the WHOIS history records of monero[.]hashvault[.]pro. Using a reverse WHOIS lookup to find other domains that contain the email address in their historical WHOIS records, we found 20 domains.
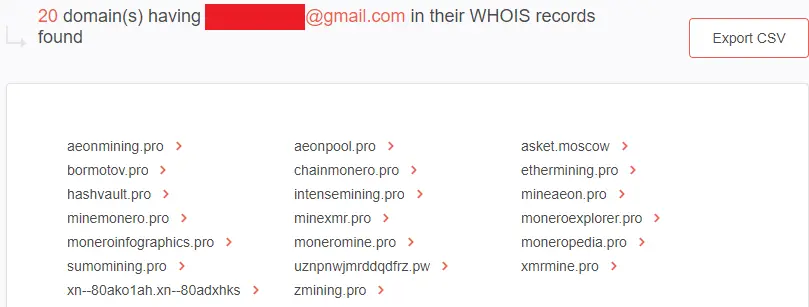
Three of the domains related to the HiddenMalware IoC were also tagged as “malicious” on VirusTotal. That said, security teams should also pay attention to them. The domains are:
- asket[.]moscow
- hashvault[.]pro
- moneroexplorer[.]pro
Domain WHOIS History of pool[.]minergate[.]com
The current WHOIS record of the domain pool[.]minergate[.]com only shows privacy-protected data. The registrant address indicated is in the U.S. However, tracing its WHOIS history tells us that from April 2014 until June 2015, the domain was registered under a person with the initials “S.W.” from the U.S., who uses a Gmail address. A company name can also be seen as the registrant organization.
A reverse WHOIS lookup using the registrant name as a search term resulted in 404 domain names. That could be due to the domain name’s commonality.
On the other hand, a reverse WHOIS lookup using the email address resulted in a shorter list of only four domains containing the company name—one of which is the root domain of pool[.]minergate[.]com and three others with different TLDs. These are:
- minergate[.]com
- minergate[.]info
- minergate[.]net
- minergate[.]org
With this intelligence, security teams can decide whether or not to block access to and from minergate[.]com and the [.]info, [.]net, and [.]org extension variants.
—
Security teams need all the help they can get to protect their organizations and fight off cyber attacks. They cannot afford to wait for IoCs to be fed to them. Instead, they have to be proactive and look for all possible domains to avoid. Tools and processes that use WHOIS history information, such as those used in this sample investigation, can be applied to known IoCs to enrich threat intelligence.







![10 Top Game Sites Not Blocked By School [2024 Updated]](https://thefutureofthings.com/wp-content/uploads/2024/10/image-25-358x358.png)