Network monitoring and diagnostic tools are used by ISP’s for daily network management operations and also by popular network apps such as peer-to-peer systems for performance optimization. Sometimes the high overhead of various monitoring and diagnosing techniques can limit the ...
Mantis Vision – Portable Scanning in 3D
The Mantis Vision F5 3D scanner The F5 3D scanner and handheld unit Image of the F5 3D scanner and handheld unit The F5-SR scanner for short range 3D scanning An Israeli company developed a small, portable hand held scanner ...
Super Precise GPS
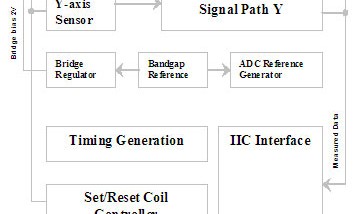
MEMSIC, a semiconductor company located in Andover, Massachusetts, has developed the new MMC212xM, a magnetic sensor that will enable greatly improved location-based services (LBS) in cellular phones and handheld GPS systems. The new component will enable greater precision and automated ...
Better Biometrics
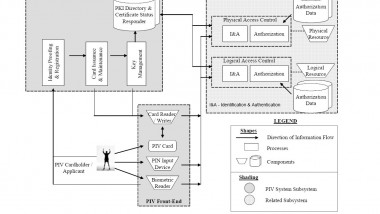
New personal identification verification (PIV) cards that offer improved protection from identity theft meet the standard accuracy criteria for federal identification cards according to researchers at the National Institute of Standards and Technology (NIST). By fall, most federal employees and ...
Fujitsu S300 Scanner Review
Fujitsu recently came up with the innovative ScanSnap S300 portable scanner. TFOT tested the mini-scanner extensively to see if its slim design and duplex capability can actually make this tiny automatic document feeder the scanner of choice for the professional ...
Fujitsu’s Palm Vein Technology
For several years, Fujitsu has been developing a new type of biometric technology expected to be more secure, reliable, and perceived as less intrusive than current biometric systems, which protect against bank card thefts, fraudulent financial transactions, and unauthorized entries. ...