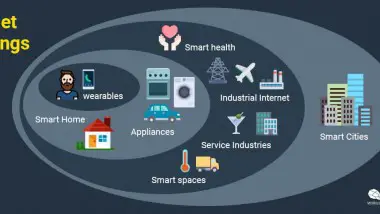
Over the last few years there has been a real boom in smart-home products, which means today, millions of people have gadgets in their home which are connected to the internet. From lights and ovens which can be turned off ...
Ways on How Technology Improves Website Hosting and Security
Technology has changed the way the web operates, and there are now systems that people can use to secure their sites. While building a new site, it’s important to integrate security into the architecture of the website. You should begin ...
THE History and Improvements In The Security Of Mobile Phones
When they have launched a few decades ago, mobile phones were huge, heavy and lacked real security functions. After all, people used it to make calls – to breathe air – so there was no real need for additional passwords ...
VPNs and Why We Need Them More Than Ever
Online privacy is a rather hot topic at the moment. Visit any news website, or open any newspaper over the last few years, and you are bound to find a story about one Silicon Valley company or another using their ...
Smart Alarm Systems: Gadgets That Protect Your Home
We live in an era where we are connected as never before. Our smartphones allow us unprecedented access to almost anything. That connection also extends to the protection of our homes; we no longer worry about whether we ‘left the ...
The Top 3 IoT Security Challenges
What is the Internet of Things? Internet of things is a network intended for communication of electronic devices. There are various ways of collecting and processing information in the functioning of the Internet of things. A perfect vision of IoT ...
Cyber Security: Password Protected
You turn on your computer and you are prompted for a username and password. The same happens when you open your email account. I know it is rather obvious to you right now, but allow me to emphasize the importance ...
6 Things You Should Be Aware Of When Using The Internet
Your privacy There are many mediums online where you might be asked to share information that you find personal, and you need to know where this information is going to be used. Every day, people give away their personal information ...
3 VMware Security Myths about Migration to the Cloud
Availability, reliability and security are the top three concerns for business information systems managers. However, these terms keep changing in meaning to reflect the underlying changes in technology. For instance, on migration to the cloud from self-hosted systems, the very ...
DoorBot – the Wireless Doorbell
The Doorbot The Doorbot app A new concept for a smart doorbell equipped with a wireless camera that can connect you to whoever is at your doorstep using your smartphone or tablet is under development and it just might change ...