Our world has never been as complex as before when we talk about security. Privacy has become a commodity. Data has become a valuable asset paving the way for more advanced and intensive surveillance technology. And the advancement of biometrics, which resulted in various types of biometric technology, becomes a layer of protection, ensuring the accuracy of results from surveillance are properly authenticated.
However, not everyone agrees on how surveillance and security are being implemented and done today. They caused divisiveness to people on how our data can be protected and still enjoy privacy. But can we still enjoy our privacy?

History
CCTV or closed-circuit television system was the first known surveillance equipment back in 1942 used in Germany during WWII to monitor rockets and weapons. Later on, the U.S. government was able to catch up with the technology and was used initially to observe the testing of nuclear bombs.
New Era of Surveillance
Fast forward to the 1990s, CCTV manufacturers keep innovating and improving the technology. They began introducing the multiplexing technique, which can now monitor feeds from multiple cameras into a single television or monitor. The 1990s was also the beginning of a new era of surveillance, CCTVs have been integrated with an Internet connection and additional devices that can be used for surveillance.
It was 1996 when surveillance cameras were first connected to the Internet, also known as IP cameras. Axis Communications launched IP cameras, and in 1999, the more improved versions were released by Mobotix using the Linux system. Since then, IP cameras and CCTVs have improved a lot when it comes to zooming range which results in a more accurate and credible result.
Surveillance cameras also help to monitor the movement of people to control the spread of the COVID19 virus with the help of drone technology. And who can forget about DVRs or Digital video recorders? It was 1998 when it was commercially released, replacing VCRs because of the ease of use, improved video resolution, and bigger memory.
The Current State of Security Systems
And we enter the 2000s. The mass production of advanced cameras and smartphones, huge data storage facilities, servers, and cloud computing with the help of high-speed Internet paved the way for mass surveillance. Mass surveillance does not limit anymore to solving isolated crimes but a tool to prevent and solve terrorism-related crimes.
On the other hand, aside from using it to call and text, smartphones can now stream to live feeds of CCTVs or use it as an IP camera. Since smartphones are taking over basic computer tasks, browsing the world wide web is as easy as brewing your favorite espresso.
However, anything we do on the Internet, like browsing, posting on social media, chats, and email, leaves marks on the Internet. These marks have become the element and pieces of information to help surveillance of any suspect.
Balancing Privacy and Security
Mass surveillance has widely been implemented all over the world to protect its citizens. But privacy regulations are still being debated among different industries, tech firms, organizations, and governments using more advanced CCTV integrated with artificial intelligence and the use of drone technology.
Data security and privacy laws keep revising. Because it seems that it is hard to achieve the level of equilibrium or balance to privacy and security, too much privacy affects so many businesses and could slow down the innovation of many products. Too much privacy can also result in unsolved crimes.
Biometric Technology
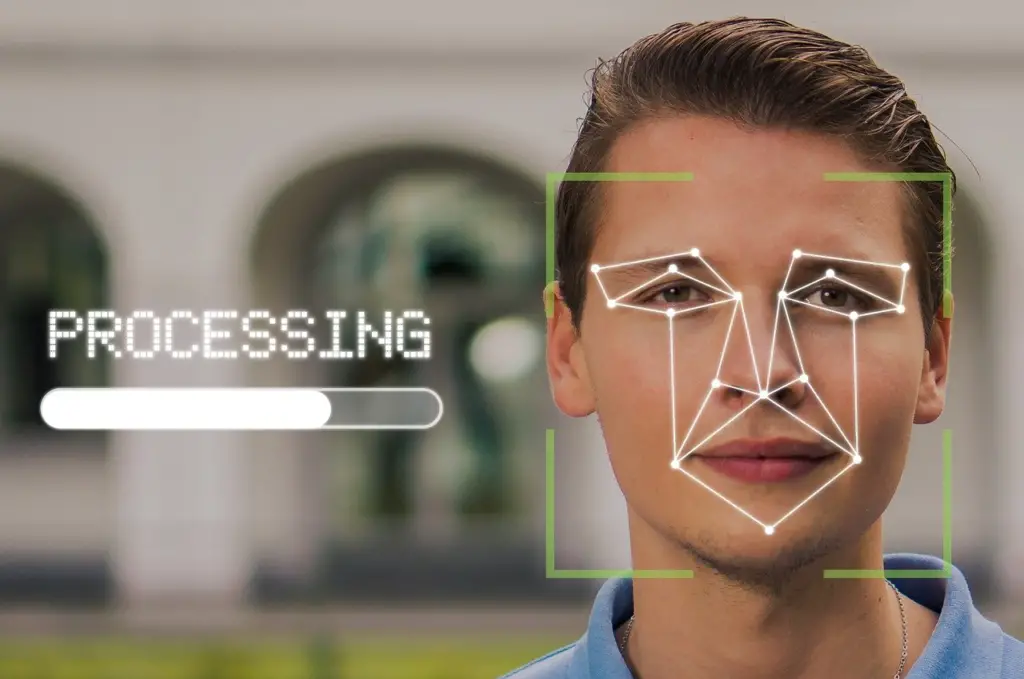
Biometrics has been an important phase of validating the identity of each one of us. Biometric technology has been widely used not only for solving crimes and fraud but for daily use like employee tracking, the replacement of passwords of our smartphones and computers, and many more.
Without proper verification and authentication, surveillance recordings would not be sufficient. But biometrics technology has been the most credible and complex way to verify and authenticate each identity.
We have summed up the various types and purposes of biometric technology.
Visual
- Face recognition
- Eyes for Iris recognition
- Eyes for Retina recognition
- Fingerprint recognition
- Ear
Behavioral
- Gait or our walking manners
- Gesture recognition
Combination of Visual and Behavioural
- Signature recognition
Combination of Visual and Spatial
- Hand Geometry recognition
- Finger Geometry recognition
Olfactory
- Odor
Auditory
- Voice for speaker identification
- Voice for speaker verification/authentication
Veins
- Vein recognition
Chemical
- DNA Matching
The credible results of biometric technology have been very useful to us. However, handling and safekeeping have been a major concern. Like facial recognition, commonly used in verifying identity, which has been integrated with artificial intelligence and a security tool replacing passwords for smartphones, becomes a subject of hacking. Tighter measures must come into place.
Final Thought
Surveillance and security will never be obsolete. It will continue to innovate, improve, and integrate new technologies to adapt to modern times. Although vulnerability to hacking and identity theft has been a major concern, we need to trust and believe that people and organizations are still willing to protect us, no matter what.
For the past 80 years, surveillance and security have helped us a lot, especially for law enforcement, who have solved and prevented crimes. With the help of evolving surveillance technology, it gives more security and peace of mind to many. The integration of biometrics technology and high-speed Internet becomes more convenient, reliable, cheaper, and available. It is our responsibility to protect our personal information. Our privacy will solely depend on our actions and decisions.